What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
The Essential Guide to Requirements Management and Traceability
Chapters
- 1. Requirements Management
- Overview
- 1 What is Requirements Management?
- 2 Why do you need Requirements Management?
- 3 Four Fundamentals of Requirements Management
- 4 Adopting an Agile Approach to Requirements Management
- 5 Status Request Changes
- 6 Conquering the 5 Biggest Challenges of Requirements Management
- 7 Three Reasons You Need a Requirements Management Solution
- 2. Writing Requirements
- Overview
- 1 Functional requirements examples and templates
- 2 Identifying and Measuring Requirements Quality
- 3 How to write system requirement specification (SRS) documents
- 4 The Fundamentals of Business Requirements: Examples of Business Requirements and the Importance of Excellence
- 5 Adopting the EARS Notation to Improve Requirements Engineering
- 6 Jama Connect Advisor™
- 7 Frequently Asked Questions about the EARS Notation and Jama Connect Advisor™
- 8 How to Write an Effective Product Requirements Document (PRD)
- 9 Functional vs. Non-Functional Requirements
- 10 What Are Nonfunctional Requirements and How Do They Impact Product Development?
- 11 Characteristics of Effective Software Requirements and Software Requirements Specifications (SRS)
- 12 8 Do’s and Don’ts for Writing Requirements
- 3. Requirements Gathering and Management Processes
- Overview
- 1 Requirements Engineering
- 2 Requirements Analysis
- 3 A Guide to Requirements Elicitation for Product Teams
- 4 Requirements Gathering Techniques for Agile Product Teams
- 5 What is Requirements Gathering?
- 6 Defining and Implementing a Requirements Baseline
- 7 Managing Project Scope — Why It Matters and Best Practices
- 8 How Long Do Requirements Take?
- 4. Requirements Traceability
- Overview
- 1 What is Traceability?
- 2 Tracing Your Way to Success: The Crucial Role of Traceability in Modern Product and Systems Development
- 3 Change Impact Analysis (CIA): A Short Guide for Effective Implementation
- 4 What is Requirements Traceability and Why Does It Matter for Product Teams?
- 5 Key Traceability Challenges and Tips for Ensuring Accountability and Efficiency
- 6 Unraveling the Digital Thread: Enhancing Connectivity and Efficiency
- 7 The Role of a Data Thread in Product and Software Development
- 8 How to Create and Use a Requirements Traceability Matrix
- 9 Traceability Matrix 101: Why It’s Not the Ultimate Solution for Managing Requirements
- 10 Live Traceability vs. After-the-Fact Traceability
- 11 How to Overcome Organizational Barriers to Live Requirements Traceability
- 12 Requirements Traceability, What Are You Missing?
- 13 Four Best Practices for Requirements Traceability
- 14 Requirements Traceability: Links in the Chain
- 15 What Are the Benefits of End-to-End Traceability During Product Development?
- 5. Requirements Management Tools and Software
- Overview
- 1 Selecting the Right Requirements Management Tools and Software
- 2 Why Investing in Requirements Management Software Makes Business Sense During an Economic Downturn
- 3 Why Word and Excel Alone is Not Enough for Product, Software, and Systems Development
- 4 Application lifecycle management (ALM)
- 5 Is There Life After DOORS®?
- 6 Checklist: Selecting a Requirements Management Tool
- 6. Requirements Validation and Verification
- 7. Meeting Regulatory Compliance and Industry Standards
- Overview
- 1 Understanding ISO Standards
- 2 Understanding ISO/IEC 27001: A Guide to Information Security Management
- 3 What is DevSecOps? A Guide to Building Secure Software
- 4 Compliance Management
- 5 What is FMEA? Failure Modes and Effects Analysis
- 6 TÜV SÜD: Ensuring Safety, Quality, and Sustainability Worldwide
- 8. Systems Engineering
- 9. Automotive Development
- 10. Medical Device & Life Sciences Development
- Overview
- 1 The Importance of Benefit-Risk Analysis in Medical Device Development
- 2 Software as a Medical Device: Revolutionizing Healthcare
- 3 What’s a Design History File, and How Are DHFs Used by Product Teams?
- 4 Navigating the Risks of Software of Unknown Pedigree (SOUP) in the Medical Device & Life Sciences Industry
- 5 What is ISO 13485? Your Comprehensive Guide to Compliant Medical Device Manufacturing
- 6 What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
- 7 ISO 13485 vs ISO 9001: Understanding the Differences and Synergies
- 8 Failure Modes, Effects, and Diagnostic Analysis (FMEDA) for Medical Devices: What You Need to Know
- 9 Embracing the Future of Healthcare: Exploring the Internet of Medical Things (IoMT)
- 11. Aerospace & Defense Development
- 12. Architecture, Engineering, and Construction (AEC industry) Development
- 13. Industrial Manufacturing & Machinery, Automation & Robotics, Consumer Electronics, and Energy
- 14. Semiconductor Development
- Glossary
Chapter 10: What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
Chapters
- 1. Requirements Management
- Overview
- 1 What is Requirements Management?
- 2 Why do you need Requirements Management?
- 3 Four Fundamentals of Requirements Management
- 4 Adopting an Agile Approach to Requirements Management
- 5 Status Request Changes
- 6 Conquering the 5 Biggest Challenges of Requirements Management
- 7 Three Reasons You Need a Requirements Management Solution
- 2. Writing Requirements
- Overview
- 1 Functional requirements examples and templates
- 2 Identifying and Measuring Requirements Quality
- 3 How to write system requirement specification (SRS) documents
- 4 The Fundamentals of Business Requirements: Examples of Business Requirements and the Importance of Excellence
- 5 Adopting the EARS Notation to Improve Requirements Engineering
- 6 Jama Connect Advisor™
- 7 Frequently Asked Questions about the EARS Notation and Jama Connect Advisor™
- 8 How to Write an Effective Product Requirements Document (PRD)
- 9 Functional vs. Non-Functional Requirements
- 10 What Are Nonfunctional Requirements and How Do They Impact Product Development?
- 11 Characteristics of Effective Software Requirements and Software Requirements Specifications (SRS)
- 12 8 Do’s and Don’ts for Writing Requirements
- 3. Requirements Gathering and Management Processes
- Overview
- 1 Requirements Engineering
- 2 Requirements Analysis
- 3 A Guide to Requirements Elicitation for Product Teams
- 4 Requirements Gathering Techniques for Agile Product Teams
- 5 What is Requirements Gathering?
- 6 Defining and Implementing a Requirements Baseline
- 7 Managing Project Scope — Why It Matters and Best Practices
- 8 How Long Do Requirements Take?
- 4. Requirements Traceability
- Overview
- 1 What is Traceability?
- 2 Tracing Your Way to Success: The Crucial Role of Traceability in Modern Product and Systems Development
- 3 Change Impact Analysis (CIA): A Short Guide for Effective Implementation
- 4 What is Requirements Traceability and Why Does It Matter for Product Teams?
- 5 Key Traceability Challenges and Tips for Ensuring Accountability and Efficiency
- 6 Unraveling the Digital Thread: Enhancing Connectivity and Efficiency
- 7 The Role of a Data Thread in Product and Software Development
- 8 How to Create and Use a Requirements Traceability Matrix
- 9 Traceability Matrix 101: Why It’s Not the Ultimate Solution for Managing Requirements
- 10 Live Traceability vs. After-the-Fact Traceability
- 11 How to Overcome Organizational Barriers to Live Requirements Traceability
- 12 Requirements Traceability, What Are You Missing?
- 13 Four Best Practices for Requirements Traceability
- 14 Requirements Traceability: Links in the Chain
- 15 What Are the Benefits of End-to-End Traceability During Product Development?
- 5. Requirements Management Tools and Software
- Overview
- 1 Selecting the Right Requirements Management Tools and Software
- 2 Why Investing in Requirements Management Software Makes Business Sense During an Economic Downturn
- 3 Why Word and Excel Alone is Not Enough for Product, Software, and Systems Development
- 4 Application lifecycle management (ALM)
- 5 Is There Life After DOORS®?
- 6 Checklist: Selecting a Requirements Management Tool
- 6. Requirements Validation and Verification
- 7. Meeting Regulatory Compliance and Industry Standards
- Overview
- 1 Understanding ISO Standards
- 2 Understanding ISO/IEC 27001: A Guide to Information Security Management
- 3 What is DevSecOps? A Guide to Building Secure Software
- 4 Compliance Management
- 5 What is FMEA? Failure Modes and Effects Analysis
- 6 TÜV SÜD: Ensuring Safety, Quality, and Sustainability Worldwide
- 8. Systems Engineering
- 9. Automotive Development
- 10. Medical Device & Life Sciences Development
- Overview
- 1 The Importance of Benefit-Risk Analysis in Medical Device Development
- 2 Software as a Medical Device: Revolutionizing Healthcare
- 3 What’s a Design History File, and How Are DHFs Used by Product Teams?
- 4 Navigating the Risks of Software of Unknown Pedigree (SOUP) in the Medical Device & Life Sciences Industry
- 5 What is ISO 13485? Your Comprehensive Guide to Compliant Medical Device Manufacturing
- 6 What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
- 7 ISO 13485 vs ISO 9001: Understanding the Differences and Synergies
- 8 Failure Modes, Effects, and Diagnostic Analysis (FMEDA) for Medical Devices: What You Need to Know
- 9 Embracing the Future of Healthcare: Exploring the Internet of Medical Things (IoMT)
- 11. Aerospace & Defense Development
- 12. Architecture, Engineering, and Construction (AEC industry) Development
- 13. Industrial Manufacturing & Machinery, Automation & Robotics, Consumer Electronics, and Energy
- 14. Semiconductor Development
- Glossary
What You Need to Know: ANSI/AAMI SW96:2023 — Medical Device Security
In this subchapter, we offer a preview of our comprehensive guide to understanding ANSI/AAMI SW96:2023 and mitigating security risks
Managing risk around a medical device’s entire lifecycle has become increasingly complex. Many devices use third-party components, which is especially true for devices that require a network to operate. This increased need for connectivity, along with other emerging threats, is putting security at the forefront of medical device industry standards.
A recent report titled “2023 State of Cybersecurity for Medical Devices and Healthcare Systems” found 993 vulnerabilities in the 966 medical products it examined—a 59% year-over-year increase from 2022. Software applications, including those that medical devices relied on to work, accounted for 64% of the vulnerabilities found.
With device vulnerability increasing, new standards aim to keep up with emerging threats. As a result, ANSI/AAMI SW96:2023 was created to help protect against threats, understand risk, and guide manufacturers in taking the most appropriate actions to enhance security. However, because the standard is relatively new, many device manufacturers are still finalizing the interpretation of how this impacts their organizational processes. If you’re still working to get familiar with the standard, we’ve created a complete guide to make the task easier.
Third-party components may increase security risk, with one study finding that software alone accounted for 64% of noted vulnerabilities.
What is ANSI/AAMI SW96:2023?
ANSI/AAMI SW96:2023 guides security risk management for medical devices, aligning with the processes included in ISO 14971:2019.
The new standard addresses the entire lifecycle of a medical device, including areas such as design, production, and post-production. It’s intended for use with AAMI TIR57 Principles for Medical Device Security – Risk Management, which addresses cybersecurity analysis, and AAMI TIR97, Principles for Medical Device Security, which guides processes for managing medical devices in the post-market space.
The goal of the new standard is to support manufacturers in ensuring that medical devices are reliable, work as intended, and don’t cause harm to patients, operators, or the environment. It also focuses on mitigating any potential risks around device failure.
RELATED ARTICLE: Understanding Integrated Risk Management for Medical Devices
Why is security for medical devices important?
Security has always been important to medical device manufacturers, which is why considerations are included in ISO 14971:2019. However, ANSI/AAMI SW96:2023 aims to deepen security-related standards.
Addressing potential security risks throughout the entire product lifecycle, including design, production, and post-production, enables manufacturers to identify and mitigate potential risks through a more focused and proactive approach. It helps manufacturers continually identify, review, and safeguard against fast-evolving threats
Understanding the security risk management process
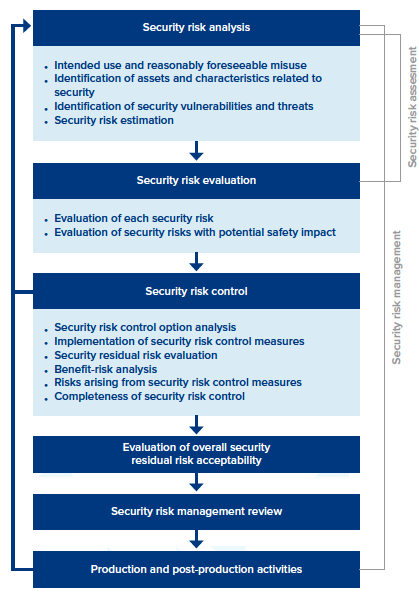
As you get up to speed with ANSI/AAMI SW96:2023, the “security risk management process” section includes details for mitigating potential threats. It includes six major sections, everything from security risk analysis to production and post-production activities. Each section contains a detailed framework, but for the sake of simplicity, we’ve highlighted a few main points for each.
The 6 Sections of Security Risk Management
- Security risk analysis. It focuses on selecting product security standards, performing threat modeling, and establishing capabilities to identify and detect security vulnerabilities across a medical device’s entire lifecycle.
- Security risk evaluation. Establishes a security assessment strategy and testing processes.
- Security risk control. Identifies, designs, and implements security risk control measures, as well as verifying the implementation effectiveness of any security risk control measures.
- Evaluation of overall security residual risk acceptability. Determine if the “security residual risk” of a device is acceptable.
- Security risk management review. A security management report is prepared.
- Production and post-production activities. Potential vulnerabilities are monitored to identify any new security risks. Also, it establishes processes to stay aware of new threats, creating security incident response plans and other measures to identify ongoing vulnerabilities.
Section 1: Security Risk Analysis
The security risk analysis focuses on selecting product security standards, performing threat modeling, and establishing capabilities to identify and detect security vulnerabilities across a medical device’s entire lifecycle. It covers:
- Security risk analysis process: It suggests that manufacturers perform a security risk analysis, and the results are recorded in the “security risk management file.”
- Intended use and reasonably foreseeable misuse: The “security risk management” file includes reference documents developed in compliance with clause 5.2 of ISO 14971. It needs to account for “the use of a medical device in a way not intended by the manufacturer, but which can result from readily predictable behavior.”
- Identification of assets and characteristics related to security: You’ll also identify potential medical device vulnerabilities such as third-party components, hardware, and software.
- Security risk estimation: You will estimate the associated “risks” for each of the identified security vulnerabilities and potential impacts on areas like confidentiality and integrity.
Section 2: Security Risk Evaluation
The security risk evaluation establishes a security assessment strategy and testing processes. A few areas it considers:
- Evaluation of each security risk: Identify each security risk area, determining if a “security reduction” is required.
- Evaluation of security risks with a potential safety impact: Consider every potential risk to determine any potential safety impacts.
RELATED ARTICLE: The Complete Guide to ISO 13485 for Medical Devices
Section 3: Security Risk Control
This section is focused on identifying, designing, and implementing security risk control measures, as well as verifying the implementation effectiveness of any security risk control measures, including:
- Security risk control option analysis: Determine if a security risk control measure is appropriate for mitigating security risks to an “acceptable level.”
- Implementation of security risk control measures: Security risk measures are selected based on the prior step.
- Security residual risk evaluation: After the security risk control measures are implemented, the manufacturer evaluates the security residential risk and records this evaluation in the security risk management file.
- Benefit-risk analysis: If a security residual risk is found to be “acceptable” using the criteria created in the security risk management plan, and further security risk control isn’t practical, the manufacturer conducts benefits versus security risk analysis.
- Risks arising from security risk control measures: The manufacturer reviews the effects of the security risk control measures to understand whether new security vulnerabilities and threats are introduced that could impact security, safety, or privacy.
- Completeness of security risk controls: The manufacturer periodically reviews security risk control activities to ensure all vulnerabilities and threats are considered and security risk control activities are complete.
Section 4: Evaluation of Overall Security Residual Risk Acceptability
After the security risk controls are implemented and verified, the manufacturer determines if the overall “security residual risk” created by the medical device is acceptable.
Section 5: Security Risk Management Review
The standard recommends a review of the execution of the security management plan before releasing a new device. According to ANSI/AAMI SW96:2023, the review should ensure:
- The security risk management plan has been appropriately implemented.
- The “security residual risk” is at an acceptable level.
- Methods are in place to gather and review details in the production and post-production phases, and leadership has reviewed and approved the plan.
Section 6: Production and Post-production Activities
The final section is focused on establishing, documenting, and maintaining a system to monitor, assemble, and review information about medical device security in the production and post-market phases. Also, it establishes processes to stay aware of new threats, creating security incident response plans and other measures to identify ongoing vulnerabilities.
In This Webinar, Learn How to Enhance Security Risk Management with ANSI/AAMI SW96:2023
ANSI/AAMI SW96:2023: is a standard which includes policies, procedures, and best practices designed to evaluate, control, and monitor potential risks involved with a medical device.
Book a Demo
See Jama Connect in Action!
Our Jama Connect experts are ready to guide you through a personalized demo, answer your questions, and show you how Jama Connect can help you identify risks, improve cross-team collaboration, and drive faster time to market.